
It was the tragic, high-profile murder of a 13-year-old girl in Southampton. Hampshire Constabulary’s huge investigation to solve the case in 2018 is now praised as an outstanding example of joint working across various teams, winning the digital investigators an international award this March.
In this edition of Force Focus, Hants’ team shares learnings from the case, including how digital forensics enabled the recovery of crucial physical evidence, and why DFUs shouldn’t shy away from analysis in the cloud.

Digital and physical crossover
In many police forces digital forensic and physical forensics are seen as different disciplines and their teams operate separately. But there can be benefits to working in a more collaborative way.
“One of the things that makes me most proud in this case is how digital informed physical forensics,” says Samantha Howard, Scientific Support Services Manager at Hampshire Constabulary.
“They’re often seen as distinct and have very different management, but here we have a real-life example where digital was enabled to lead physical. The crossover between the two isn’t exploited enough.
“Investigators asked the digital forensic team to help identify locations of a potential suspect. The traces left on his digital devices gave investigators the route of the suspect, meaning they could target the search and ultimately find an item of clothing. That clothing gave a biological link between the suspect and victim.
“It was an extraordinarily large investigation. Without the digital input, the search would have taken far longer or may not have succeeded.”
Sheer scale
During the investigation Hants received more than 300 reports from members of the public, collected around 2,300 exhibits, searched a total area of 610,000 square metres and analysed 11,200 hours of CCTV footage from 140 premises.
The vast quantity of data and potential evidence is nothing new to force DFUs, most of which are facing increase numbers of devices in each case or have backlogs of devices awaiting analysis.
Dennis Mosell, Digital Forensic Manager at Hants’ High Tech Crime Unit, says:
“The main challenge is the sheer scale of items seized. We had a recent case with 40 to 50 devices. It’s not only the devices you initially find in person but ones you discover that are linked by the cloud.
“You may think you've got the golden device on day one, and it’s tempting for investigators to want all the data and want it now. But in this case and every case, we have to ensure we do it right way and keep the integrity of the devices so they can be used as evidence in court.”

Digital forensic challenges
So, what process does a digital forensic investigator have to go through to find the right evidence? What about when a suspect refuses to provide passwords, like in this case? And how much harder is it when investigating in relatively new areas of tech like the cloud that don’t have supporting legislation and established ways of working?
This was one of Hants’ first cases to explore the cloud, and it turned-up many challenges, not to mention many gruelling hours of manual analysis.
“We have a standard operating procedure for this now but back in 2018 we didn't have much,” says Nathan Wright, the Hants investigator responsible for cloud data gathering who was personally commended by the case’s judge. “We also didn't have cloud examination software available so a lot of it was manual.”
Nathan was provided with some devices seized from the suspect and tasked with piecing together his route during the key window of time.
“We used a variety of cloud accounts that transfer across multiple devices,” he says. “We analysed the existing devices to see what was there in the 1s and 0s, then we start pulling the thread.
“There was a wearable fitness device which was linked by the cloud to a smartphone and a tablet. Once we got the cloud account details and were able to access the cloud, we identified that there was another smartphone. That was the key device where we found hidden Facebook accounts with recent messages between the suspect and victim. Eventually we picked out what he did for that day, when he went to work, what he did in the days before.”
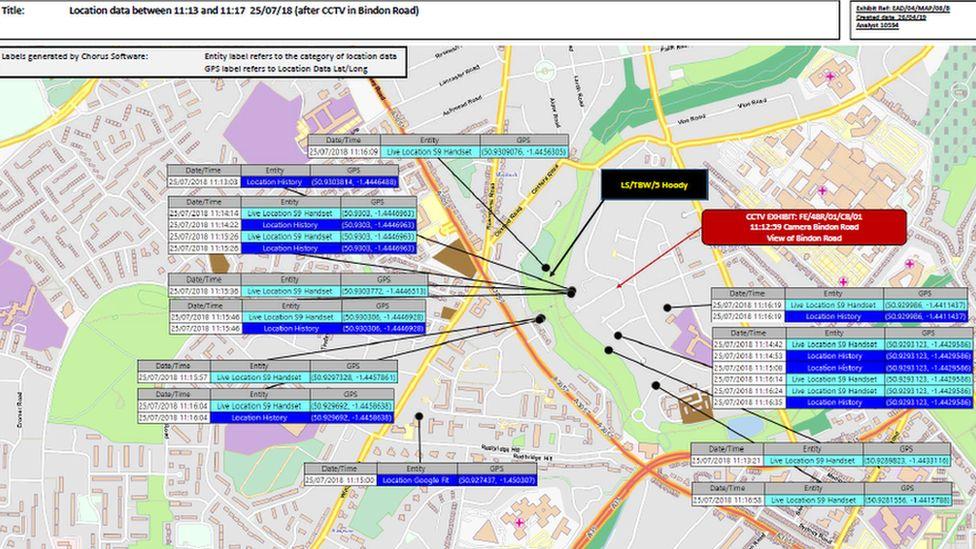
The cloud provides real potential for investigations but accessing it isn’t simple, as Nathan explains. Outdated legislation and poor collaboration from technology providers are both key blockers.
“For instance, legislation to seize or gain access to cloud accounts are still not fully formed. The use of PACE for example is under contention throughout the UK as it is open to different interpretations whereas other covert authorities are difficult to obtain.
“In this case, the suspect refused to give his log-on details, so we used S49 legislation which you can use to remand people on failure to give up passwords. It’s important to know what authorities to use and how to get into data.
“Even when we do have the authorities, we have to attack different service providers with different methods, and data is often obfuscated. Back in 2018 the tools weren’t very advanced so we did it manually. We had one particular problem with GPS location data, as the tools were parsing locations incorrectly, so we had to manually go through it. The technical side of that was really in-depth, down to the binary.
“Now, the tools are better but APIs change so quickly and we’re always having to find other methods. There were no white papers or best practice on how to do this. We had to get it peer reviewed and managed to find three or four people in law enforcement that were also doing this.”
The last word
What advice does Hants’ team give to other forces? The first is to exploit the connections between digital and physical forensics during investigations. The second, for digital forensic units, is to look at cloud examination as a discipline and a service of its own, a third area after phones and computers.
“Don't shy away from cloud just because you think it's too difficult,” says Dennis. “There’s a wealth of information out there, and if anyone has any issues they can reach out to us.”
About this article
Force Focus is a series of in-depth articles with people across the FCN network, sharing insights and ideas from one force to others. If you’d like to share a story from your organisation for a future Force Focus, or want to be put in touch with the Hants team to discuss cloud analysis, please contact us.